Timeline
Significant events in the history of information previously covered on Beyond the Frame.
Representative Taylor Greene Spreads QAnon Claims in Congress on the Night of the Capitol Invasion
“It’s been proven that these [voting] machines are connected and that they can be hacked.” †
From the article Truth Storms the Capitol
Podcaster Joe Rogan Signs With Spotify
Joe Rogan announced an exclusive deal with Spotify that sent data archivists scrambling to save the media and community discussions surrounding his show on YouTube. The deal is worth more than $100 million according to Anne Steele of The Wall Street Journal, “Spotify Strikes Podcast Deal With Joe Rogan Worth More Than $100 Million.”
From the article Aggregators, Publishers, and the Third Way
Apple and Google Announce Bluetooth Contact Tracing Efforts
Apple and Google decided to bake an automated exposure notification service into their portable devices. The software will enable intra-device information exchange over Bluetooth while keeping each individual’s identity a secret.
From the article The State of COVID-19 Exposure Notifications
NotPetya Malware Appears
The NotPetya malware first appeared in 2017, on the eve of Ukrainian Constitution Day. It affected thousands of systems in over 65 countries. Maersk, the Danish shipping company, lost $300 million in revenues and was forced to replace 4,000 servers. Even still, Ukraine was the malware’s clear target, suffering 80% of all infections.
From the article Disinformation Strategies and Tactics
Bret Victor Publishes “What Can a Technologist Do About Climate Change?”
Midway through What Can a Technologist Do About Climate Change?, Victor opines that public discourse on climate relies on “tips, soundbites, factoids, and emotional rhetoric” rather than “evidence-grounded models.” He suggests a solution for working with and discussing profound problems: better tools for model-driven debate, model-driven reading, and model-driven authoring.
From the article Information's Role in Facing Climate Change
“Fuck the EU.” Malinformation Effort
An anonymous source posted a conversation between the US Assistant Secretary of State, Victoria Nuland, and the US Ambassador to Ukraine, Geoffrey Pyatt. Amidst all the political banter, one line stood out, “Fuck the EU.” The leaked audio was a crude effort to sow dissension between the US and its EU allies during a tense moment in Ukraine - a move that would clearly help Russian interests.
From the article Disinformation Strategies and Tactics
Amazon Removes Purchased Copies of '1984'
“Justin Gawronski, a 17-year-old from the Detroit area, was reading ‘1984’ on his Kindle for a summer assignment and lost all his notes and annotations when the file vanished. ‘They didn’t just take a book back, they stole my work,’ he said.” †
From the article How Ebooks Have Poisoned Electronic Ink
Facebook Introduces Targeted Ads
“‘Facebook Ads represent a completely new way of advertising online,’ Zuckerberg told an audience of more than 250 marketing and advertising executives in New York. ‘For the last hundred years media has been pushed out to people, but now marketers are going to be a part of the conversation. And they’re going to do this by using the social graph in the same way our users do.’” †
From the article An Identity Through Time
Walter Murch Edits “Cold Mountain” on an Off-the-Shelf Macintosh G4
Cold Mountain was not the first digitally edited feature film. But the $80 million picture was the first of its size to be cut on Apple's Final Cut Pro and off-the-shelf Power Mac G4s. It was subsequently nominated for seven academy awards including Best Film Editing.
From the article Untangling Non-Linearity
The Dot-Com Bubble Peaks
The Nasdaq index peaked at 5,132.52 on March 10, 2000 - doubling in value over the previous year. By October 10, 2002, the Nasdaq plummeted to 1,108.49.
From the article Fix My Code
ArtByte: The Magazine of Digital Arts and Culture
ArtByte was a glossy magazine dedicated to covering net.art and many other forms of digital art. It was distributed across the United States until it ceased publication in 2001.
From the article Fix My Code
Framework for Global Electronic Commerce
“For electronic commerce to flourish, the private sector must continue to lead. Innovation, expanded services, broader participation, and lower prices will arise in a market-driven arena, not in an environment that operates as a regulated industry.” †
From the article A Different Internet
The Net Art Generator by Cornelia Sollfrank
“A smart artist makes the machine do the work! The net.art generator is a computer program which collects and recombines material from the Internet to create a new website or a new image. The WWW-interface of the easy-to-use program requires the user to enter a title which then functions as the search term, and to enter a name as author. The resulting images and websites are stored online in an archive from where recent results can be downloaded.” †
From the article Fix My Code
Italian Law Protecting Citizens Regarding the Processing of Personal Data
Article 30 establishes The Italian Data Protection Authority. Stefano Rodotà is named the first president. Rodotà believed that privacy protected the dignity of the person - an essential part of a functioning free society.
From the article A Different Internet
A Declaration of the Independence of Cyberspace
“Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather.” †
Network Solutions Charges for Domain Names
NSF allows Network Solutions to begin charging for domain name registration services, which were perviously free for .com, .net, .org, .edu, and .gov top-level domains.
From the article Gallery 404
The Identity Politics Biennial
The annual exhibition at the The Whitney Museum of American Art focused explicitly on issues around gender, race, and sexuality for the first time. It was dubbed “the identity politics biennial.” Identity became a central focus of cultural discourse as internet pioneers promised to emancipate people from their corporeal limitations.
The Domain Name System is Standarized (RFCs #1034 & #1035)
Paul Mockapetris publishes the initial designs for a human-readable Domain Name System that maps network addresses (188.40.28.20) to human-readable names (schmud.de). His design allows the lookup tables required to scale across the entire world. †
From the article An Identity Through Time
Les Immatériaux
Les Immatériaux was presented at the Centre Pompidou in Paris. It chronicled many of the confluent developments of media, art, theory, and technology. Christiane Paul suggested that the exhibition “argued that the immaterial is matter subjected to interaction and conceptual processes,” highlighting the shrinking gap between our lives in cyberspace and the physical space. †
From the article Software Preservation in Networked Art
Do Artifacts Have Politics?
“It is obvious that technologies can be used in ways that enhance the power, authority, and privilege of some over others, for example, the use of television to sell a candidate. [...] But we usually do not stop to inquire whether a given device might have been designed and built in such a way that it produces a set of consequences logically and temporally prior to any of its professed uses.” †
From the article How the Consumer Computer is Consuming Computing
Minitel
Minitel, a popular public computer network, comes online in France. This network is used to provide online services to the general public.
From the article Galley 404
The Finger Protocol (RFCs #742 & #1288)
Finger, originally written in 1971, is the granddaddy of status updates. Running finger dschmud@heartland.bradley.edu on TCP port 79 “return(ed) a friendly, human-oriented status report on a particular person in depth.” †
From the article An Identity Through Time
Radio Shack announces the TRS-80.
The TRS-80 benefited from Radio Shack's tremendous distribution advantage over 1977's other two debuting consumer computers - the Commodore PET 2001 and the Apple II.
From the article To Catch a Mouse Make a Noise Like a Cheese
The United States Privacy Protection Study Commission Issues Their Report
The Privacy Protection Study Commission generated 162 recommendations to help protect citizens against the intrusive nature of digital data collection, storage, and dissemination. They found that the Privacy Act of 1974 “had not resulted in the general benefits to the public that either its legislative history or the prevailing opinion as to its accomplishments would lead one to expect.” These recommendations were never codified into law. †
From the article Personal Privacy
California Constitutional Right of Privacy Amendment
A 1972 amendment to the California Constitution that included the “right of privacy among the ‘inalienable’ rights of all people. The amendment established a legal and enforceable right of privacy for every Californian. Fundamental to this right of privacy is the ability of individuals to control the use, including the sale, of their personal information.” †
From the article Personal Privacy
The First Ebook is Uploaded
Michael S. Hart founded Project Gutenberg when he uploaded a copy of the United States Declaration of Independence to the ARPANET. It was the first text of its type to be shared on the fledgling computer network.
From the article How Ebooks Have Poisoned Electronic Ink
Project Minaret at the National Security Agency
“The project, which became known officially as Minaret in 1969, employed unusual procedures. NSA distributed reports without the usual serialization. They were designed to look like HUMINT reports rather than SIGINT and readers could find no originating agency. Years later the NSA lawyer who first looked at the procedural aspects stated that the people involved seemed to understand that the operation was disreputable if not outright illegal.” †
From the article MLK and “Domestic Terrorism”
The ARPANET
The ARPANET, an early military computer network, comes online in the United States. The network is used to coordinate information and share computing resources.
From the article Gallery 404
RFC #1: Host Software
The first two Request For Comments (RFC) describe how computers and routers (knowns as IMPs) would be used to form a computer network (the ARPANET). †
Cybernetic Serendipity
Cybernetic Serendipity was an exhibition of electronic, cybernetic, and computer art curated by Jasia Reichardt, shown at the Institute of Contemporary Arts, London, England. It was organized in three sections: 1. Computer generated work, 2. Cybernetic devices-robots and painting machines, 3. Machines demonstrating the use of computers and the history of cybernetics.
From the article Software Preservation in Networked Art
“The Computer As A Communication Device”
“First, life will be happier for the on-line individual because the people with whom one interacts most strongly will be selected more by commonality of interests and goals than by accidents of proximity. Second, communication will be more effective and productive, and therefore more enjoyable. Third, much communication and interaction will be with programs and programmed models [...]. And, fourth, there will be plenty of opportunity for everyone to find his calling, for the whole world of information, with all its fields and disciplines, will be open to him.” †
From the article On the Internet, We Are Either Artists or Bureaucrats
J.C.R. Licklider Coins the Term “Narrowcasting”
‘The Carnegie Commission Report on Educational Television [...] proposed interconnecting PBS stations via satellite, and a supplementary paper by MIT professor and Internet visionary J.C.R. Licklider outlined several future scenarios for television including one that foresaw a multiplicity of television networks aimed at serving the needs of smaller, specialized audiences. “Here,” stated Licklider, “I should like to coin the term ‘narrowcasting,’ using it to emphasize the rejection or dissolution of the constraints imposed by commitment to a monolithic mass-appeal, broadcast approach”’ †
From the article Truth Storms the Capitol
Ted Nelson Introduces the Term “Hypertext”
The foundation of today's World Wide Web was introduced to the public in “Complex information processing: a file structure for the complex, the changing and the indeterminate.” Nelson explains, “Let me introduce the word ‘hypertext’ to mean a body of written or pictorial material interconnected in such a complex way that it could not conveniently be presented or represented on paper.” He would continue to refine the concept for several decades. †
From the article Untangling Non-Linearity
The First Message Is Sent Using the Moscow–Washington Hotline
The first text is sent from the United States to Russia over the Moscow–Washington hotline: “THE QUICK BROWN FOX JUMPED OVER THE LAZY DOG'S BACK 1234567890”. The June 1963 Hot Line Agreement represents the first time the two nations took action to avert an accidental nuclear war.
From the article Information Warfare Is Without Limits and So Are Its Consequences
David Padwa Co-Founds Basic Systems With Francis Mechner
“Firm specialized in educational and curricular technologies as well as the provision of systems integration services in education and training markets. In 1964 Xerox Corporation acquired Basic Systems; continued as division executive at Xerox and Director of Planning for educational markets.” †
From the article Be Here Now
Logic Theorist Presented at the Dartmouth Summer Research Project on Artificial Intelligence (AI)
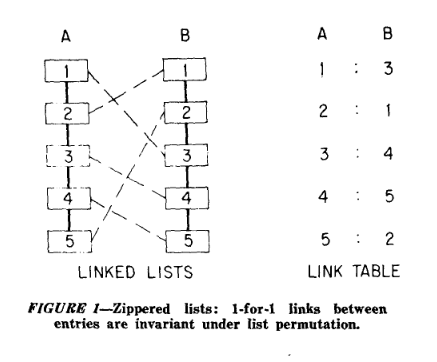
Cliff Shaw, along with Allen Newell and Herbert Simon, developed the Information Processing Language (IPL) to implement Logic Theorist, as existing languages lacked the capabilities for solving abstract problems like the mathematical proofs in Whitehead and Russell's Principia Mathematica. A major innovation in IPL was the linked list, a dynamic memory allocation technique crucial for AI and a foundational element in John McCarthy's LISt Processing language (LISP).
From the article Untangling Non-Linearity
George Orwell Publishes “Nineteen Eighty-Four”
“The essence of oligarchical rule is not father-to-son inheritance, but the persistence of a certain world-view and a certain way of life, imposed by the dead upon the living.” †
From the article “Nineteen Eighty-Four”
Bombing of the Amsterdam Population Registery
Dutch resistance members, including Willem Arondéus, Gerrit van der Veen, and Dr. Frieda Belinfante, orchestrated a bombing of the Amsterdam Population Registry on Saturday, March 27, 1943. Their goal was to inhibit the Nazi's ability to track and deplort Jews and other targets of terror. The operation managed to destroy over 15% of the records but many of the particpants were later captured and executed by the Nazis. †
From the article What If Data Is a Bad Idea?

Bach Writes “Herr, gehe nicht ins Gericht mit deinem Knecht”
Musical notation falls short of capturing the composer’s intent, the performer’s performance, and the audience’s experience. However, it is the reason we have access to the music of Bach and Beethoven. Musical scores embody information that has traveled through the centuries, slowly and subtly mutating along the way.
From the article Notes From the Ambient Church
